Ensure Service Availability and Operational Continuity with Azure Availability Zones
SHARE THE BLOG
Overview
The IT environment encounters challenges day after day. Businesses that heavily rely on IT face growing obstacles in two key areas: Data Protection and Continuous Service Availability. IT teams are finding it harder to maintain compliance with vendor best practices as the IT ecosystem becomes more and more complicated.
The most fundamental requirement for business continuity is to maintain critical operations during a crisis and to recover with the least amount of downtime possible. A business continuity plan considers a variety of unforeseen calamities, including fires, epidemics, disease outbreaks, cyberattacks, and other external threats.
An organization can keep up-to-date copies of its data in multiple locations, not just in the primary data center, thanks to technologies like Azure Availability Zones. If one location is disabled, this ensures that data access continues uninterrupted and prevents data loss.
• Why Business Continuity is Important?
At a time when downtime is unacceptable, business continuity is critical. There are numerous causes of downtime. Cyberattacks and extreme weather appear to be getting worse as a threat. A business continuity plan that takes into consideration any potential disruptions to operations is crucial.
During a crisis, the plan should allow the company to operate at least at a minimum level. By responding quickly to outages, business continuity helps the organization maintain its resilience. Businesses with strong continuity save money, time, and reputation. Financial, personal, and reputational damage may result from an extended service interruption.
• Multi-Availability Zone
In this blog, we will have a closer look at a new option we now see in the portal when we create a virtual machine, it’s the Multi-Availability Zone, an unexplored concept. Why am I given the option to create multiple availability zones when building a VM, and what is it exactly?
The main importance of the Multi-Availability Zone is that you can select multiple availability zones and create one VM per zone.
• Availability Sets
Deploying Azure VMs in an availability set will not protect your application from failures associated with the operating system or application-specific errors. However, placing virtual machines in an availability set will provide protection against network outages, physical hardware failures, and power interruptions within one Azure data center.
• Availability Zones
Availability zones are similar to availability sets. While availability sets are used to protect applications from hardware failures within the same Azure data center, availability zones protect your applications or services from interruptions across Azure data center failures.
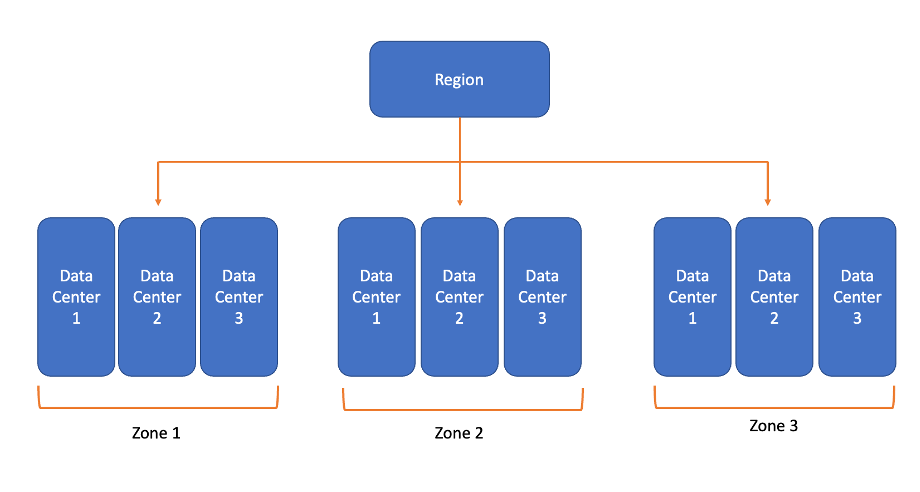
An availability zone is a unique physical location that exists within an Azure region. Every availability zone contains at least one data center within the region. Each of these data centers has its own power, its own networking, and its own cooling. To ensure resiliency, every enabled region in Azure consists of at least three separate zones that are physically separated. It is this physical separation that protects applications from data center failures.
So azure subscription maps independently. One subscription may point to data centers AZ1, and a different subscription may point to the same AZ or another, hence we should understand that there’s no consistency over different subscriptions.
The idea of Zone or DCs grouping is each set of these data centers will have independent power, cooling, and networking. It’s not just about resiliency at the physical building for maybe a fire or flood but if there was some power outage or water problem and networking.
Each of these different sets has resilient isolated services, so a power failure for example for this AZ1 wouldn’t affect these other AZ or sets of data centers.
Availability Zones Benefits
- Azure VM Availability Zones offer industries best uptime SLA (99.99%)
- Azure’s availability zones ensure high availability and resiliency as a part of your disaster recovery and business continuity strategy. Its high-performance architecture comes with a built-in strategy and is highly flexible.
- Azure High Availability helps eliminate any single failure point across a regional network design. It connects at least 3 physically distinct Data Centers placed strategically in each region, considering more than 30 risk factors and viability criteria.
- Synchronous Data Replication further helps contain the impact of Data Center failures by maintaining a latency perimeter of fewer than 2 milliseconds between Azure availability zones.
• Availability Services Redundancy
Let’s deep dive into Azure services redundancy and multiple data centers. Individual data centers would help protect businesses from any disruptions at a data center level but there are common services such as cooling, networking, power, etc., so what also happens is grouping sets of these data centers grouped into availability zones.
Zone Redundant Services
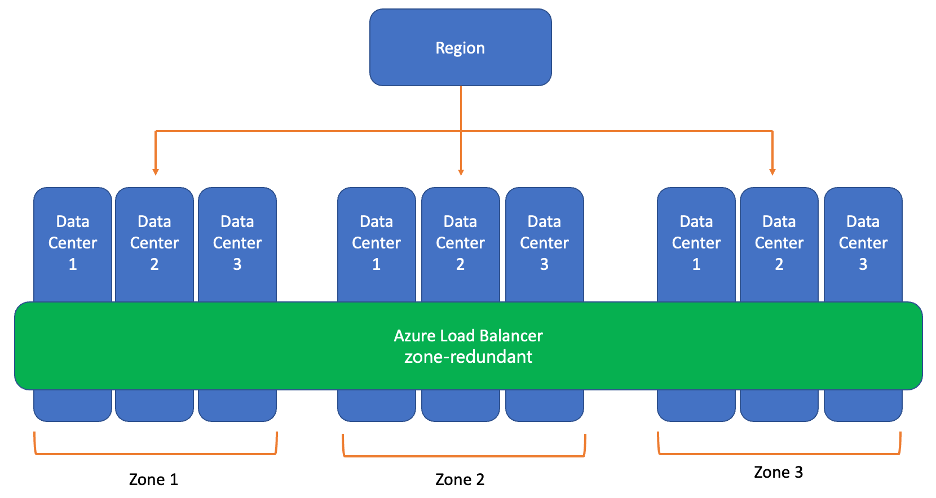
When leveraging the Availability Zones, we can think about Azure Standard Load Balancer which can be zone redundant. So now when thinking about deploying such a service, you can deploy it as a zone redundant.
In a matter of fact, we just span it into multiple availability zones behind the scenes and the traffic would be served by a single IP address. This single frontend IP address will survive zone failure. The frontend IP may be used to reach all (non-impacted) backend pool members no matter the zone. One or more availability zones can fail, and the data path survives if one zone in the region remains healthy.
As illustrated in the image, the frontend’s IP address is served simultaneously by multiple independent infrastructure deployments in multiple availability zones. Any retries or reestablishment will succeed in other zones not affected by the zone failure.
Zonal Services
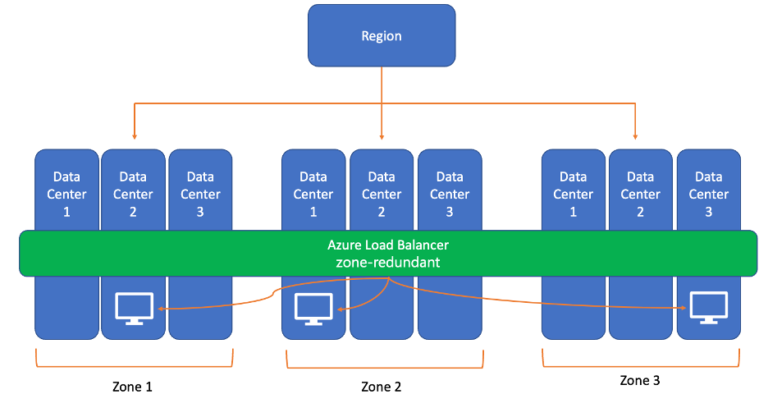
Other services especially the ones that are compute-focused, they can’t just be zone redundant, like a virtual machine running on a host it’s virtualizing the CPU, it’s also virtualizing the memory of a physical box. Having CPUs spread over multiple data centers is just not feasible.
You could create a VM in AZ1 so that VM would get pinned to a specific data center in that AZ and you can create it in that availability zone.
So, let’s think about doing zone redundancy for computing services that are zonal by nature.
- Create a VM scale set zone redundant
- Create an AKS node pool that sits on top of a VM scale set
- Carry out an app service plan
Well, we must create an instance in each zone, if it was a VM scale set or an AKS node port or app service plan, we should have our instances distributed across these zones. They can all run the workload, and often they’ll sit behind another zone redundant service like a standard load balancer that’s so redundant to balance the requests.
As illustrated above I can have VM, AKS, App services plan, and other zonal services as zone redundant by distrusting them across different zones and placing them behind Zone redundant services like Azure load balancer.
Create Your Azure Workloads with the AZ Option
• Create Azure Virtual Machine with Multiple Zones.
When you jump to Azure Portal under Create A Virtual Machine blade you will have the option to enable or disable availability based on your need, Azure offers a range of options for managing availability and resiliency for your applications. Architect your solution to use replicated VMs in Availability Zones or Availability Sets to protect your apps and data from datacenter outages and maintenance events.
To use availability zones, create your virtual machines in one of the supported Azure Region
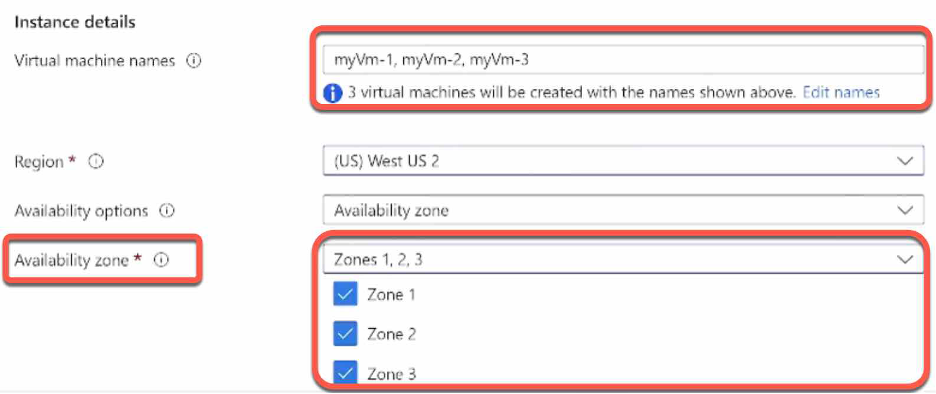
Some users will now see the option to create VMs in multiple zones.
For the Availability zone, the drop-down defaults to Zone 1. If you choose multiple zones, a new VM will be created in each zone. For example, if you select all three zones, then three VMs will be created. The VM names are the original name you entered, with -1, -2, and -3 appended to the name based on the number of zones selected. If you want, you can edit each of the default VM names.
Also, if you want to create a load balancer, go to the Networking tab > Load Balancing > Load balancing options. You can choose either an Azure load balancer or an application gateway.
Some users will now see the option to create VMs in multiple zones.
For the Availability zone, the drop-down defaults to Zone 1. If you choose multiple zones, a new VM will be created in each zone. For example, if you select all three zones, then three VMs will be created. The VM names are the original name you entered, with -1, -2, and -3 appended to the name based on the number of zones selected. If you want, you can edit each of the default VM names.
Also, if you want to create a load balancer, go to the Networking tab > Load Balancing > Load balancing options. You can choose either an Azure load balancer or an application gateway.
• Create App Service Plan,
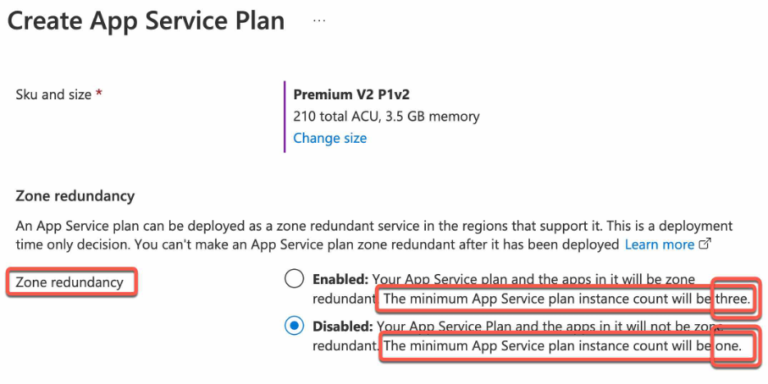
As highlighted in the previous section an App Service plan can be deployed as a zone redundant service. And this can be done only during the deployment time. You can’t make an App Service plan zone redundant after it has been deployed.
When you jump to Azure Portal under Create App Service Plan blade you will have the option to enable or disable zone redundancy based on your need, as illustrated below, keep in mind if you enable it the minimum App Service plan instance count will be three.
Bespin Managed Services for a Seamless Infrastructure Management
Leveraging Bespin Global’s Managed Services Offering for Infrastructure Management, businesses can enhance their Azure Availability Zones setup to achieve seamless service availability and operational continuity. Here’s how each service in our Managed Services supports this:
- Proactive
Monitoring Services: Identifies potential issues before they impact
service availability.
- Infrastructure
Operations Management Services: Ensures consistent and reliable
infrastructure performance.
- Backup
and Restore Services: Facilitates quick recovery from unexpected
disruptions across zones.
- Well
Architected Review (WAR): Optimizes architecture for high availability
and resiliency.
- Compute
Vulnerability Scan: Detects and mitigates vulnerabilities to maintain
secure, uninterrupted operations.
- Cost
Optimization: Enhances resource efficiency while maintaining
performance.
- Patch
Management: Keeps systems up-to-date, reducing downtime risks from
security vulnerabilities.
- Cloud
DevOps Operational Services: Automates deployment across zones for
consistent high availability.
- Database
Management Services: Maintains data integrity and availability with
zonal redundancies.
- Advanced
Network Management Services: Optimizes network traffic to ensure
performance across multiple zones.
- Disaster
Recovery Management Services: Prepares for and manages failovers
seamlessly.
- Managed
FinOps Services: Monitors costs while ensuring optimal allocation of
resources for critical applications across zones.
Talk to our Experts: Ensure Service Availability & Operational Continuity.
– Enhance IT services’ continuity and availability
– Make use of cloud-based BC and DR capabilities with cost optimization
– Benefit from our proven-and-true methods.
– Integrate private, public, and hybrid cloud options to protect data.
– Safeguard the financial health and reputation of your company.
– Reduce the chance of disturbance.
– Accelerate your journey to hybrid cloud and extend your datacentre
– Establish availability and recovery goals to satisfy organizational needs.
– Create your apps with resilience features depending on the needs for availability.
– To increase reliability and reduce costs, use availability zones and disaster recovery planning as needed.
Mahmoud Atallah
Mahmoud Atallah
Start the Conversation Today
Let's Talk