How to Strengthen Your Cloud Security Posture & Governance
-
Mahmoud Atallah
- October 31, 2022
- 6:00 pm
Share the Blog
Overview
The cyber-attack landscape has rapidly evolved in recent years and the SolarWinds hack, one of the biggest cybersecurity breaches of the 21st century, was the crack. Today, the costs that result from a single breach could reach millions of dollars without any exaggeration. Quite devastating for an organization, right?
To keep up with the sophistication of today’s threats, the traditional models are failing to provide the full visibility and control you need to secure your environment. Moving to the cloud and addressing security and governance matters in a cloud environment brings more complexity for organizations where regulatory rules are constantly changing, and the cost of compliance increases as well. Keeping up with all this isn’t easy.
In this article, we will closely examine how Microsoft Defender, a security model that quickly adapts to the reality of the world we live in, allows all organizations and governmental entities to appropriately secure their environments whether they are on Azure or on-premises. We will also demonstrate how to leverage the cloud security posture management feature in Microsoft Defender to ensure maintaining a proper security posture and being compliant with various regulatory compliance such as FedRAMP, CMMC, and CIS.
We will also showcase how to secure your workloads within the azure environment and on-prem resources such as storage accounts, containers, VMs, and more.
What are the most common security challenges?
Visibility into the security compliance · Increase in number of sophisticated attacks · Complexity of managing a multi-cloud environment
The very first challenge: the visibility into the security compliance
Last year in 2021, the world witnessed progressive cyber-attacks and we all remember the SolarWinds hack where the cost of a breach was estimated to be almost 4.24 million dollars! Building cloud environments brings more complexity for organizations and 92 percent of them are embracing their strategies in the Cloud but very few of them have learned how to maximize security within those new environments.
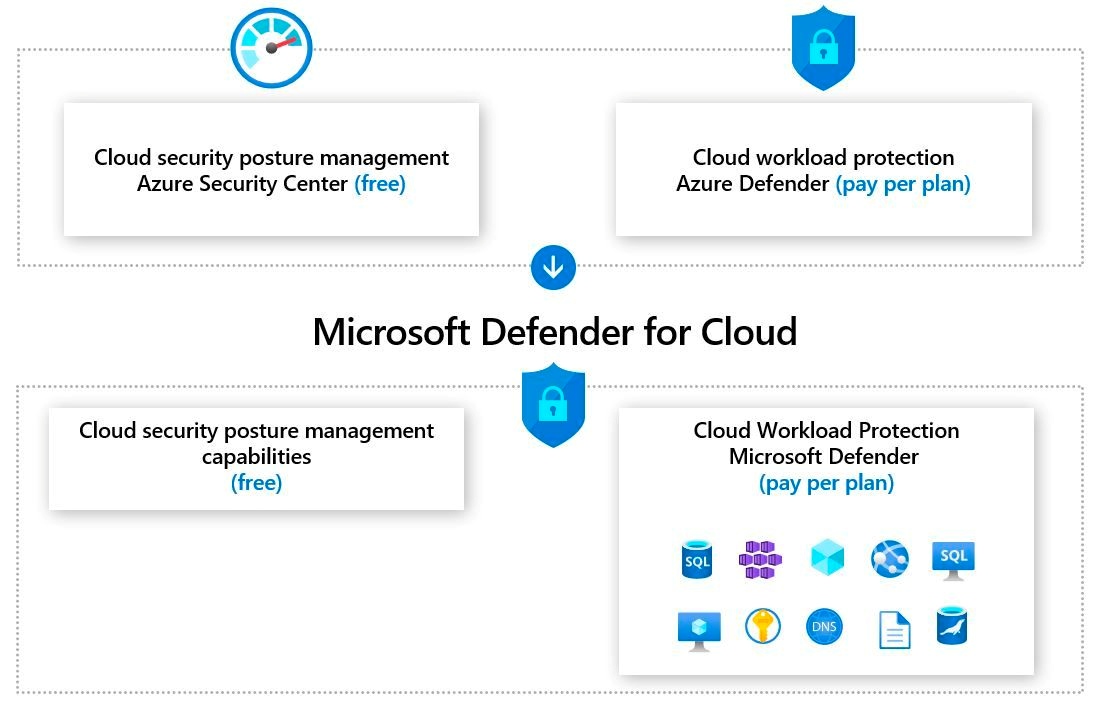
1· Microsoft Defender for Cloud
 Microsoft Defender is an Azure native security service deployed across different types of cloud and hybrid environments. It provides a full security stack in Azure, on-prem, hybrid, and multi-cloud environments as well.
Microsoft Defender is an Azure native security service deployed across different types of cloud and hybrid environments. It provides a full security stack in Azure, on-prem, hybrid, and multi-cloud environments as well.
It offers complete management of the security posture in Azure by using a security score and leveraging a standardized compliance security assessment benchmark to evaluate the security of the environment and providing you with a visible score of your security posture as well as compliance for each of those standard controls. It also detects threats and protects your workloads, either if your VM is running on Azure, or on-prem, and even on AWS or GCP. It also provides full support of protection for Azure resources and along with that full vulnerability assessment and management.
Microsoft Defender has the capability of responding to threats when found during the assessment and mitigating the incident and the alert, and those mitigations can be operated either manually or can be fully automated.The response automation can be using tools such as logic apps and can be integrated with other tools such as (sentinel, teams, outlook, ITSM Products such as slack, ServiceNow, or others)
What makes Defender better than others?
Built-In with Azure
- No Deployment, Just Enable
- Built into the resource provisioning process
- Broadest protection coverage
- Remediate with a click
- Free Cloud Security Posture Management
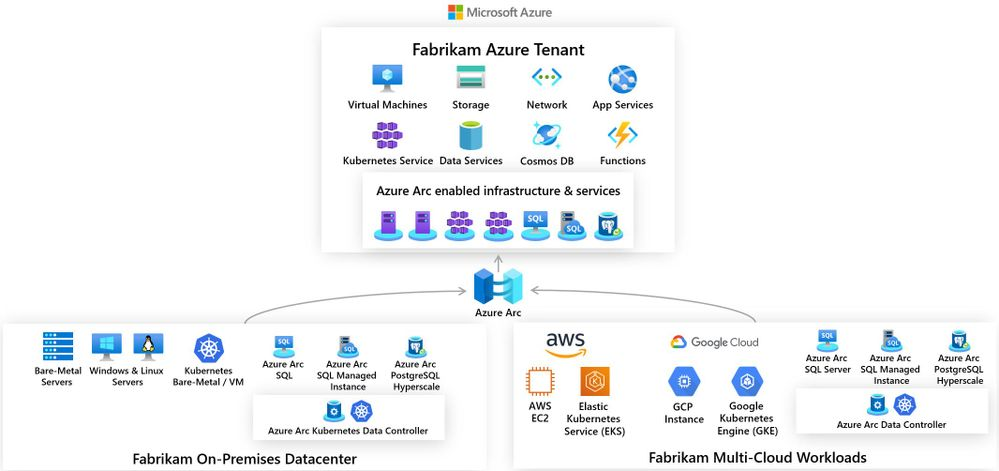
Multi-Cloud and Hybrid Support
- Auto-provisioning for new resources
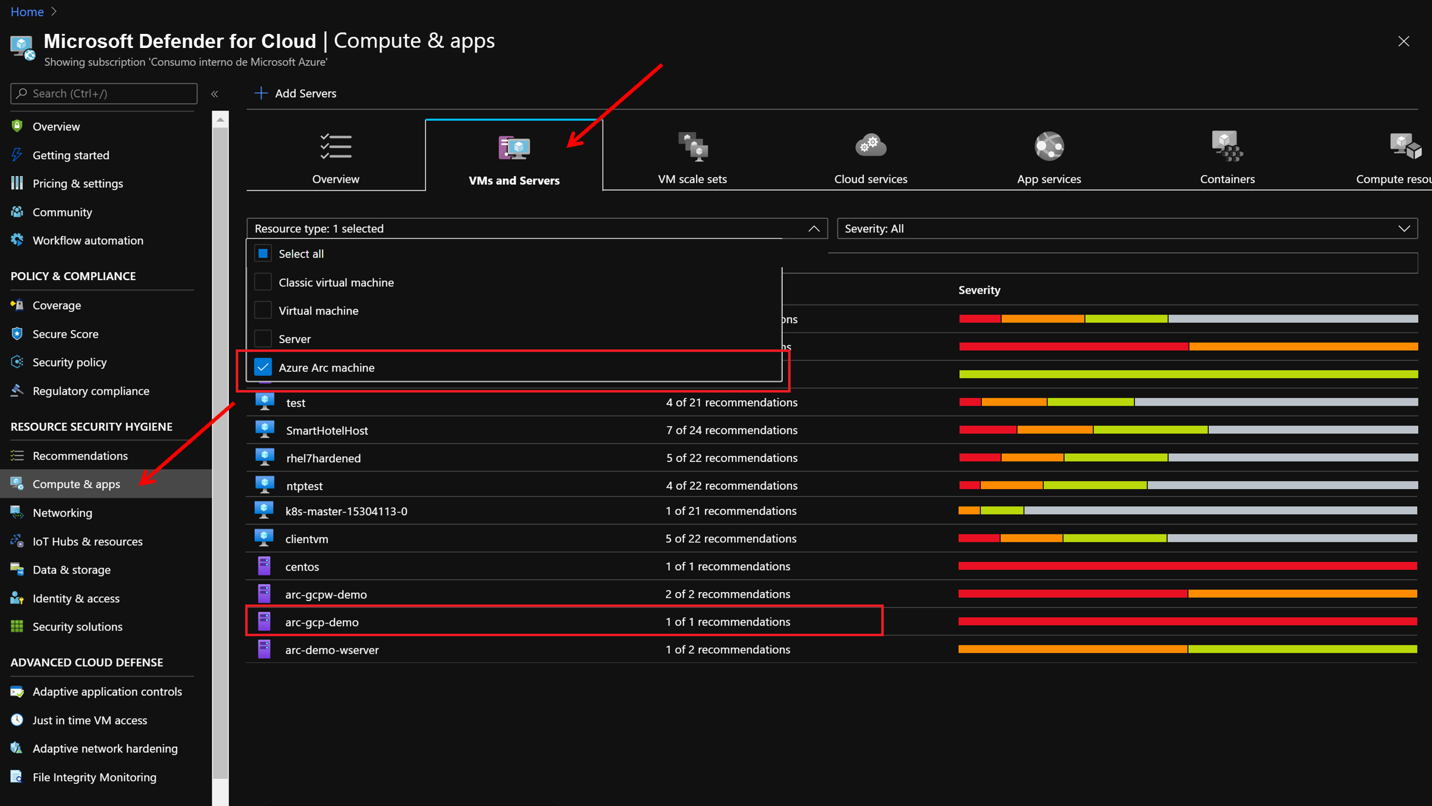
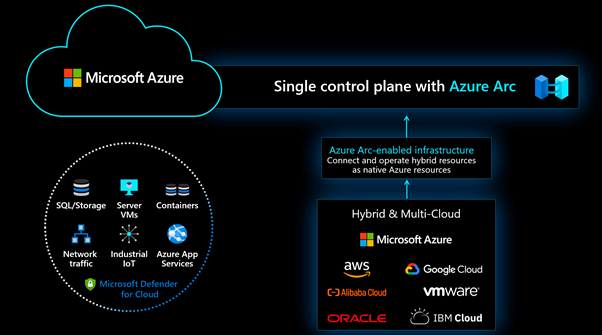
- Onboard on-prem and other cloud resources Like AWS, GCP, Alibaba Cloud with Azure Arc
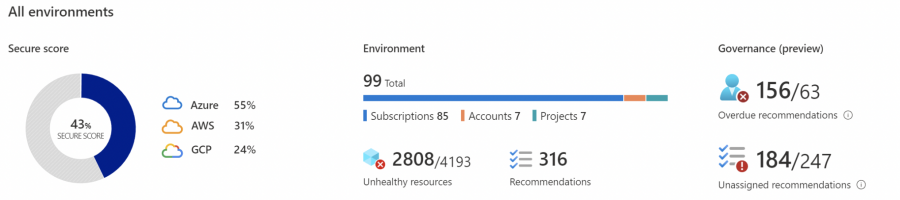
Secure Score for Multiple environments
- Birds-eye view of the security posture
- Prioritized security recommendations
- Track and manage your security posture state over time
- Implement security best practices
- Enable enhanced security features
- Remediate security configurations
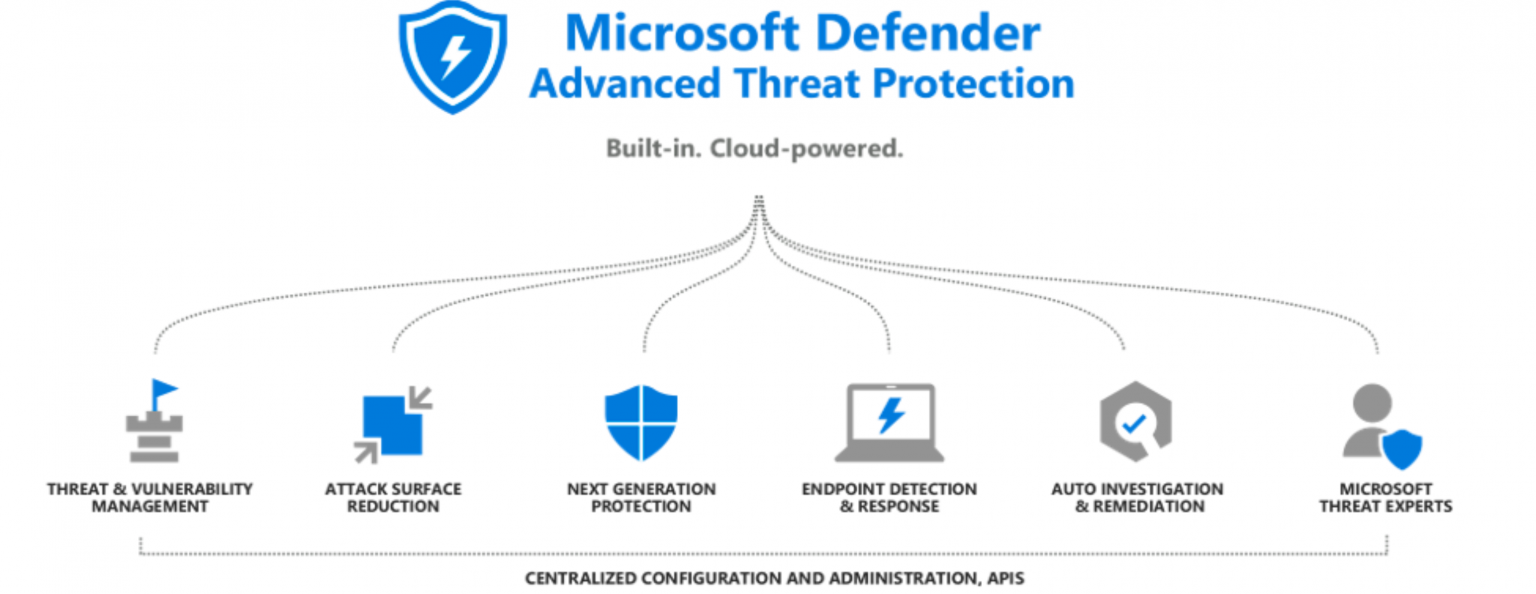
Advanced Threat Protection
- Workload-specific signals and threat alerts
- Deterministic, Al, and anomaly-based detection mechanisms
- Leverage the power of Microsoft Threat Intelligence with 24 trillion signals daily
- Advanced protection for VMs, databases, containers, web apps, networks, and more.
Microsoft Defender Capabilities for different Roles
Security Operations
Responsibility:
- Around-the-clock threat hunting, investigation of breaches, and mitigation of incidents
Product Use Cases:
- Leverage workload-specific threat detection and response mechanisms to identify attacks, investigate alerts and incidents, and quickly mitigate threats

2· Holistic management of your security posture in the cloud
The Security Dashboard
Centralized Posture View
Your security posture across Azure in one place
Focused views
Easily access deep dive views for security posture, resource inventory, workload protection, and more
Top insights front and center
· Understand which recommendations to prioritize
· See your most attacked resources and take action
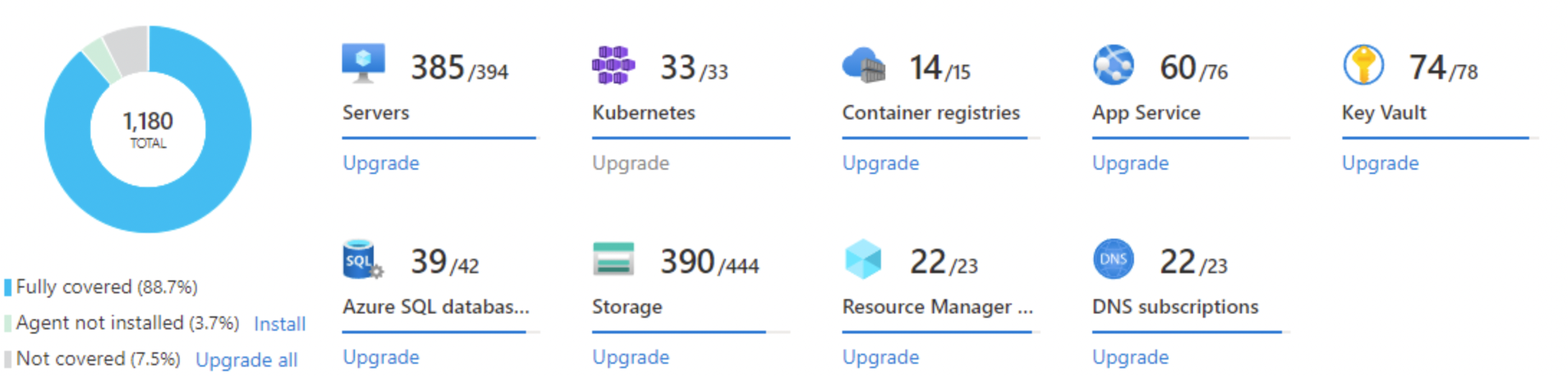
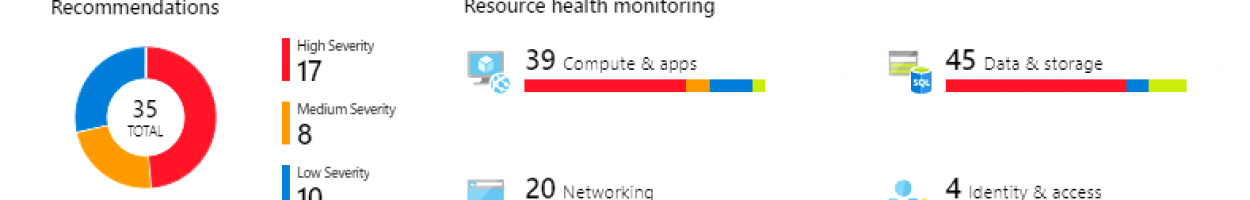
Security Posture - Secure Score
- Assess and implement best practices for security and compliance
- Cover all critical cloud resources across the network, access, compute, databases, your service layer, and more
- Hundreds of out-of-the-box recommendations
- Create custom recommendations to meet organizational requirements
- Use “Fix” or a Logic App to remediate with a single click or enforce policies to avoid configuration drifts
- Improve and track your secure score and overall security posture over time
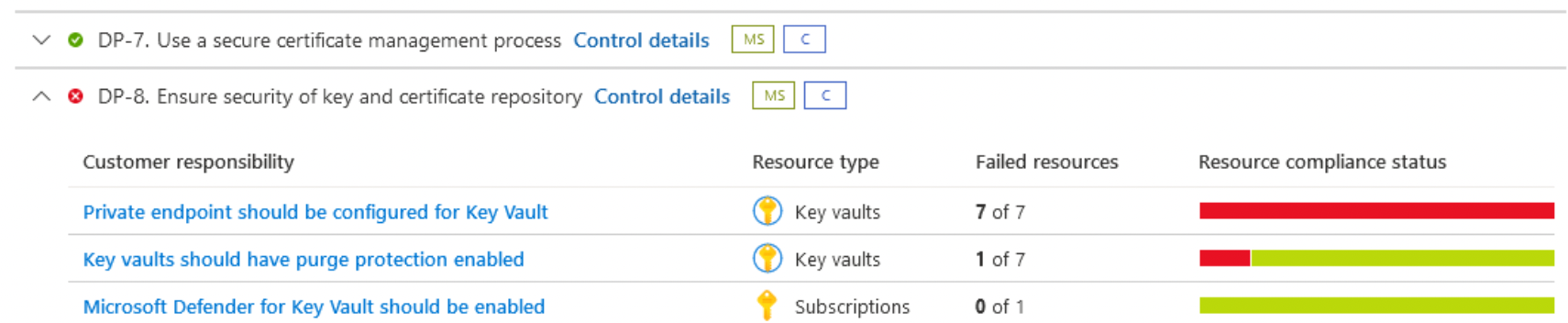
Compliance assessment and management
- Assess and manage your compliance status with a continuous assessment of your cloud resources
- Use Industry standards, regulatory compliance frameworks, and vendor-provided benchmarks to implement security and compliance best practices.
- Create custom recommendations to meet unique organizational needs
Current Supported Compliance Controllers by Cloud Defender
PCI · NIST · SOC · ISO · HIPAA · Azure Security Benchmark · CIS · CMMC · FedRAMP · DOD
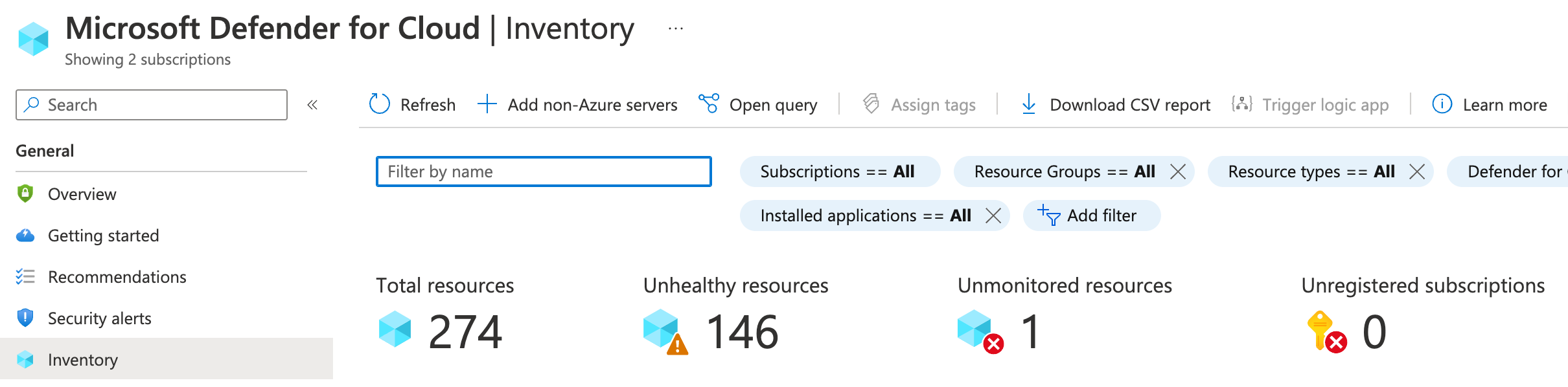
Use asset inventory to manage your resources' security posture
The asset inventory page of Microsoft Defender for Cloud Inventor Cloud provides a single page for viewing the security posture of the resources you’ve connected to Microsoft Defender for Cloud.
- Which of my subscriptions with enhanced security features enabled have outstanding recommendations?
- Which of my machines with the tag ‘Production’ are missing the Log Analytics agent?
- How many of my machines tagged with a specific tag have outstanding recommendations?
- Which machines in a specific resource group have a known vulnerability (using a CVE number)?

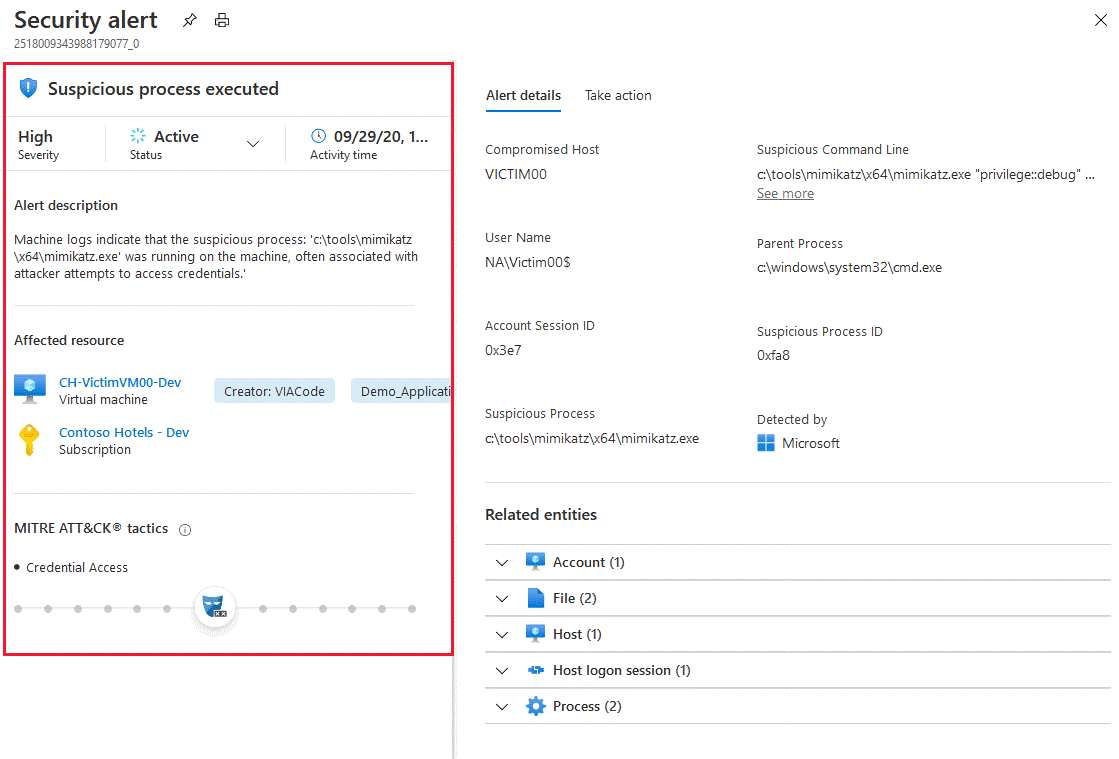
Threat Protection for all layers on the cloud and On-Prem
Threat detection
Prioritized alerts across compute, databases, the cloud service laver, and more
MITREATT&CK® framework mapping
Understand the effect across the adversary’s attack lifecycle
Leading threat intelligence
Highly sophisticated & resource-specific alerts based on Microsoft’s global threat intelligence
Vulnerability management
Identify and remediate vulnerabilities before they are exploited
Alert correlation
Prioritize more easily with connected alerts that are grouped into incidents
3· Protect your workloads in the cloud and on-premises
- Use detections that are built for the unique attack vectors of each resource type, built on the powerful insights of Microsoft Threat Intelligence
Reduce your attack surface by continuously scanning workloads to identify and manage vulnerabilities
Automatically protect new workloads as soon as they are deployed
Integrate with your SIEM for easy management of incidents.
Deploy Microsoft Defender for Cloud threat protection to your workloads anywhere with Azure Arc
Respond and automate
- Leverage “Quick Fixes” for the fastest way to implement recommendations
- Automate threat alert responses with Azure Logic Apps and use the apps of your choice to create intelligent workflows
- Connect to Microsoft Sentinel and easily move between the portals when investigating and managing incidents
Strengthen your Cloud Security Posture Today with BESPIN GLOBAL
- Enable Defender for Cloud to assess your security posture
- Fix your top 5 Secure Score recommendations today
- Start a free trial to protect your workloads
- Onboard AWS, GCP and on-prem workloads with Azure Arc