Building a Stronger Line of Defence: How Microsoft's AI-driven SIEM Can Strengthen Your Security Infrastructure
- Naqash Ahmed
- March 30, 2023
- 8:17 am
Share the Blog
Overview
Nowadays, many organizations worldwide are heavily investing in optimizing their security infrastructure due to hackers using ingenious ways to breach their data or applications. To achieve a high level of security, organizations have taken significant measures, including implementing advanced, automated, and AI-based solutions that can proactively prevent malicious activities from penetrating their perimeter
The deployment of these solutions requires not only a substantial investment but also individuals with the expertise to operate them and comprehend the necessary precautions to safeguard their environment. In this blog, we will focus on Microsoft’s AI-driven SIEM (Security Information and Event Management) from both a technical and business perspective.
What is Microsoft Sentinel?
Microsoft Sentinel is a SIEM and SOAR (Security Orchestration, Automation, and Response) solution that provides customers visibility for any attack detection, and malicious campaigns including but not limited to ransomware and phishing. It uses data connectors of various categories ranging from Microsoft-owned or any third-party e.g., Azure AD, Azure Storage, Azure KeyVault, Amazon Web Services, SAP, Apache HTTP Servers, Akamai, etc.
Sentinel has four stages or capabilities as shown in the below picture:
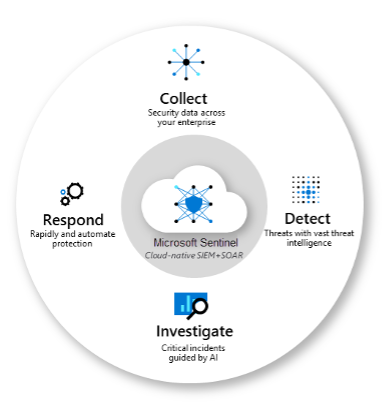
After configuring the data connectors, Sentinel initiates its operations by gathering the relevant logs and data points necessary for its functioning. The detection part uses workbooks that have defined rules to investigate the threat and to specify the coverage of the threat based on publicly available MITRE ATT&CK knowledge base techniques. The investigation involves security team intervention to check, analyze and understand the alert generated from Sentinel which also contains information like evidence, severity, status, and a timeline of Incident resolution progress until it is closed. The last stage is responding to the incidents either via a playbook containing some resolution steps, tagging it, changing the severity, or assigning an owner to the incident from the security team to attend to the incident and take appropriate action.
Why use Microsoft Sentinel?
Organizations considering implementing Microsoft Sentinel in their environment must have a clear understanding of the reasons behind their decision. To address this question, let us break it down into three key reasons that may apply to such an organization.
· High Value of Effort
Legacy or on-premises solutions typically require a significant amount of effort, including cabling, networking, and maintenance, which collectively demands a large workforce. For instance, if a high-priority alert causes a business downtime, numerous individuals may need to be engaged in diagnosing, investigating, troubleshooting, and resolving the issue using on-premises security solutions.
· High False Positives
With growing data ingested in legacy solutions, it will end up with more alerts having false positives which will be difficult to find out without any AI-based solution. It will also impact the resolution timeline for each incident which would eventually breach the customer support SLA and may cause financial damage to the service provider.
· Cost Effectiveness
The most crucial factor is the cost. Classical solutions hosted on-premises take more labor, effort, time, and maintenance and, hence, expensive capital is required. For example, ingesting more data from any source in such old solutions would require additional disks or drives which is going to increase costs.
Features of Microsoft Sentinel
Let us jump into highlighting some features in Microsoft Sentinel that make it unique and more productive than any other SIEM + SOAR solution.
- Scalable: Whether it’s users, devices, applications, or on-premises, you can get the telemetry to Sentinel from these objects across multiple clouds.
- Simplify: Onboarding subscriptions and data sources are easily managed with a single pane of the portal. No need for hiring infrastructure engineers for deploying.
- Seamless: Customers do not need to intervene during the onboarding process of Sentinel, it will only take an Azure Monitor agent (aka Log Analytics agent) to be installed in the machines to collect the logs.
- High Available: Sentinel is a cloud-based product and does not require any load balancer to make it available as it already has one built-in.
Business Value of Microsoft Sentinel
In a recent study governed by Microsoft itself and carried out by Forrester Consulting – an independent consultancy provider with research-based findings to help business leaders’ success in their organizations – on the economic impact of using Microsoft Sentinel, they interviewed different companies who have invested in Sentinel or moved from legacy solution to Sentinel. The results were extremely in favor of Sentinel in terms of costs, risks, and efforts.
Here are the results concluded after the study was completed:
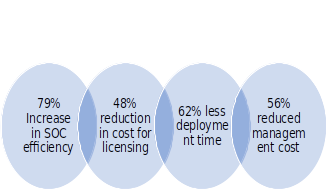
Above were calculated results but during the study, there were also unquantified conclusions that also make Sentinel apart from other alternative solutions. For example:
- Integration with other Microsoft products – Being a Microsoft-powered product, Sentinel has deeper integration with other Microsoft products that include but are not limited to Cloud App Security, Defender for Endpoint, and Microsoft 365. The logs ingested from these products provide more insights into what is going on in other SaaS applications.
- Automated workbooks – With Sentinel, every action can be automated using workbooks, so the SOC team members have more time to invest and focus on other projects.
- Bring-Your-Own-ML (BYO-ML) – Resources with expertise in ML (Machine Learning) and having “love” for data can bring their own data models into Sentinel to fight against the threats and make it more optimized. Sentinel provides Jupyter Notebooks to write and test data models.
To sum up, Sentinel has the potential and capabilities that any SMB or enterprise would require to take its IT security to the next level with less expenditure and high productivity.
At Bespin Global’s Security Operation Center (SOC) Sentinel is used as a crucial tool against combating breaches, malware, anomalies, privilege executions, brute force attacks, and many other types of suspicious actions which can lead to disasters for the customer if not proactively monitored. Our SOC engineers are well-informed about Sentinel and run pre-defined or custom workbooks on customers’ resources to scan for any suspicious activities and then report back with their recommendations provided by Sentinel itself.
Contact our experts to leverage the services of Microsoft Sentinel and achieve:
- Higher efficiency in SOC resources.
- Onboard existing or new machines and applications on Sentinel seamlessly.
- Get support from our security engineers to help implement Sentinel.
- Proactively monitor and neutralize threats using efficient Sentinel workbooks.

